No need to ADSI or LDIFDE Tools to configure the “Fine Grained Password Policy” in windows 2012 RC. All it’s done by GUI “Graphical User Interface”. It’s pretty simple and cool. As Microsoft Certified Trainer, my students found many difficulties when configuring PSO with the ADSI Tool.
1. The first step: “ Active Directory Administrative Center”
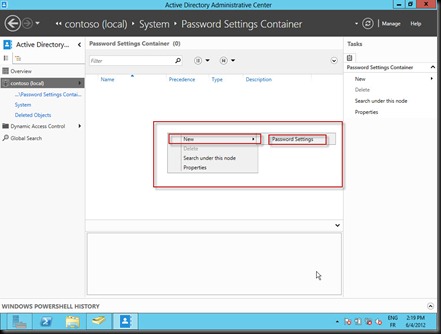
Remember, with windows 2008, we find the PSO object already created in a special container called “Password Setting Container”, under the “System” Container. So let’s go there…
2. Create the PSO object
Double click the container called “Password Setting Policy”, then, let’s do a right click…. Amazing, we can create the PSO object here. So simple…
3. A pretty cool GUI
This is the GUI to create a PSO object, I created “My first PSO Object” as you see in the following picture, the GUI is divided into two parts, the first one for the configuration purpose and the second to apply the created PSO to a user or group.
Best regards.